| This is documentation for Semarchy xDM 5.3 or earlier, which is no longer supported. For more information, see our Global Support and Maintenance Policy. |
Configure the authentication in Azure
This page explains how to configure the authentication for a Semarchy xDM instance deployed on Azure, including authentication to Microsoft Entra ID.
| Microsoft Entra ID (ME-ID) is the name of the identity and access management service formerly known as Azure Active Directory (AAD). To learn more about this name change, see the documentation on the Microsoft website. |
Default authentication configuration
Semarchy xDM is configured by default to use the built-in authentication. A first administrator user is created with the admin account and password that you have configured during the deployment.
Connect with this user to create new users, configure identity management, or to configure Microsoft Entra ID authentication as explained below.
Configure Microsoft Entra ID
Register the application in ME-ID
-
In the Azure portal, select Microsoft Entra ID.
-
Under the Manage section in the navigation pane, select App registrations, and then click New registration.
-
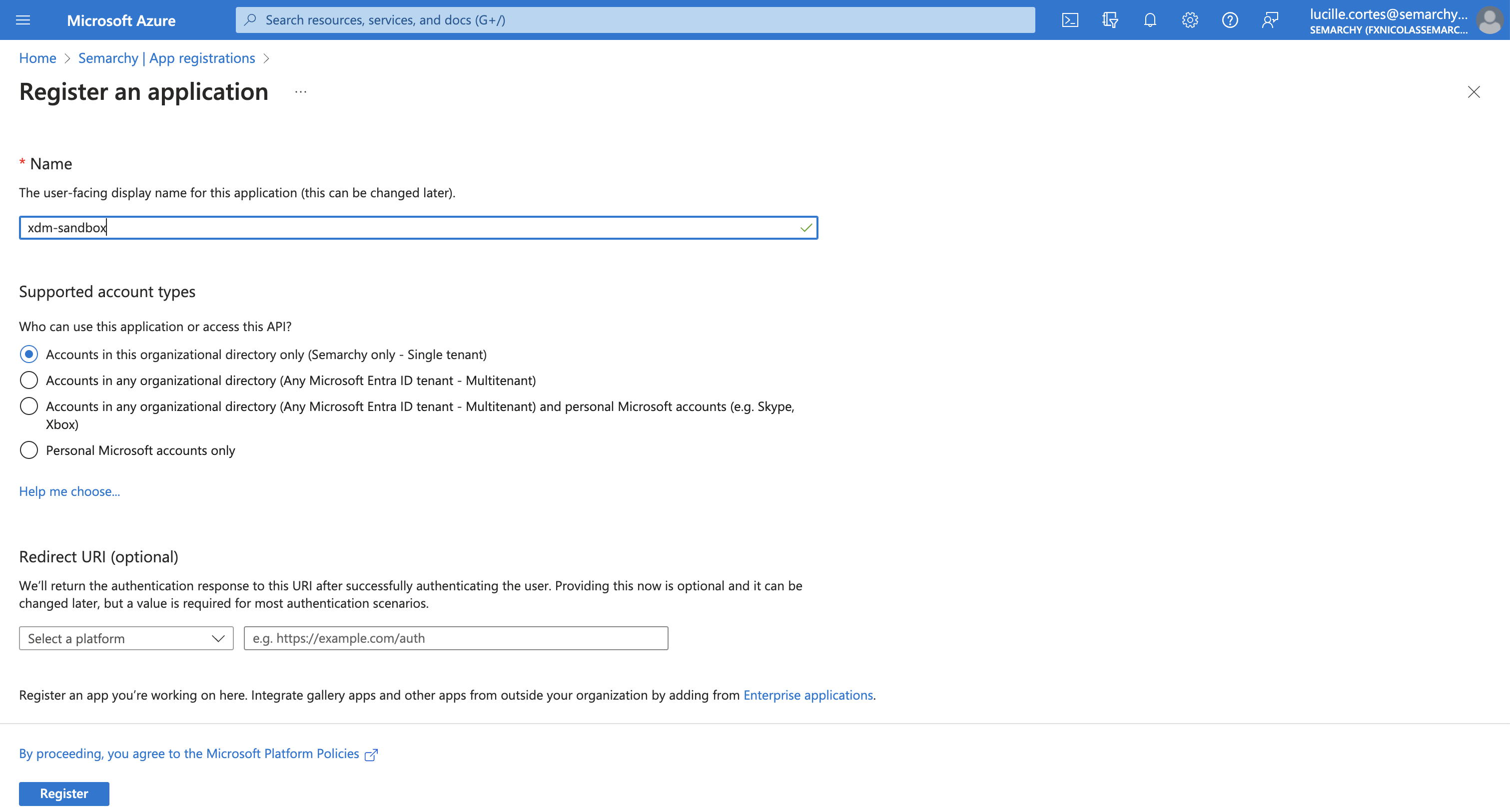
In the Register an application page, enter the following information:
-
Name: type a name for the registered application (e.g., the name of your instance).
-
Supported account types: select who can use this application.
-
Redirect URI: leave this section empty.
-
| You will set the Redirect URI parameters once you have configured the identity provider in Semarchy. |
-
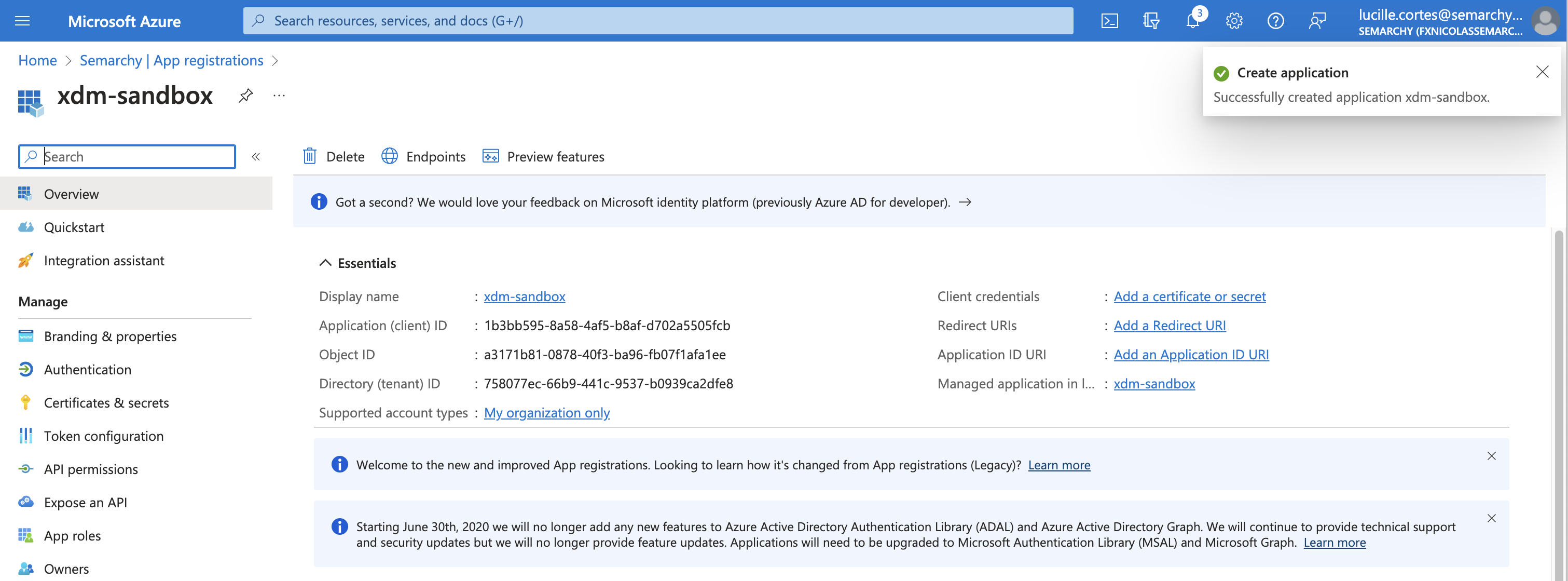
Click Register. The application registration is created and opens.
-
Under the Manage section in the navigation pane, select Certificates & secrets, and then click New client secret.
-
In the Add a client secret side sheet that appears, describe the client secret in the Description field, and then click Add.
-
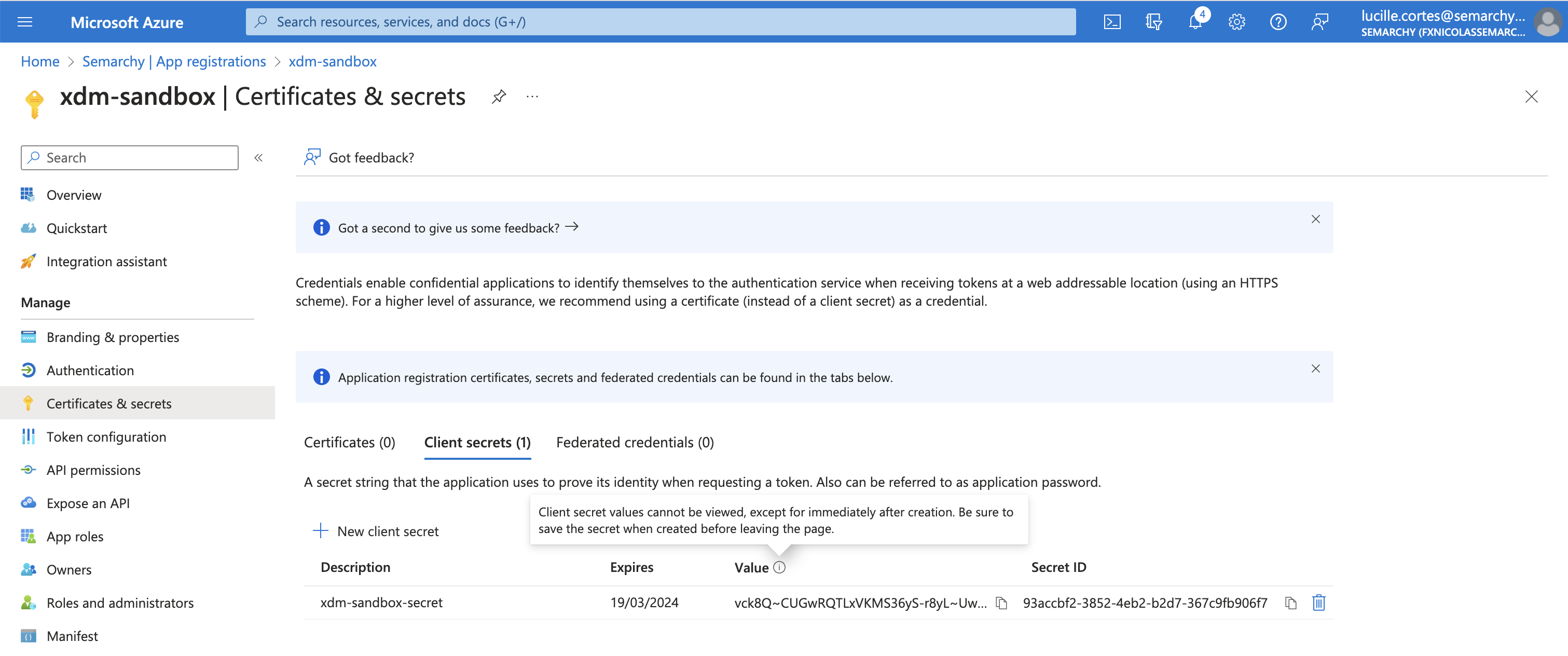
The secret is created. Note the client secret in the Value column, as you will need it later in the configuration.
-
Under the Manage section in the navigation pane, select API permissions, and then click Add a permission.
-
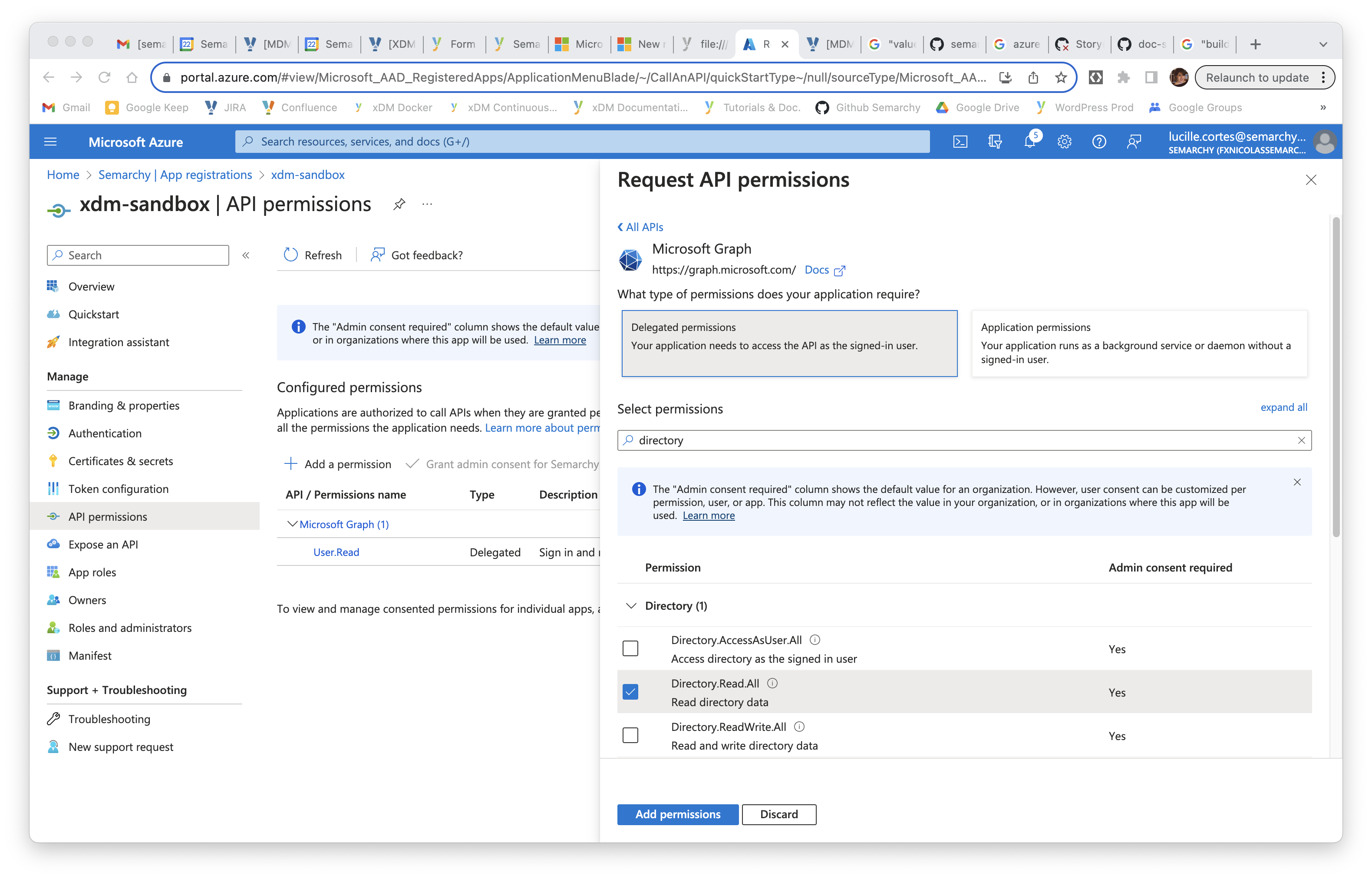
In the Request API permissions side sheet that appears, select Microsoft Graph.
-
Select Delegated permissions and then enter
directoryin the Select permissions search field to filter the permissions. -
Expand the Directory section and select the Directory.Read.All permission, then click the Add permissions button.
-
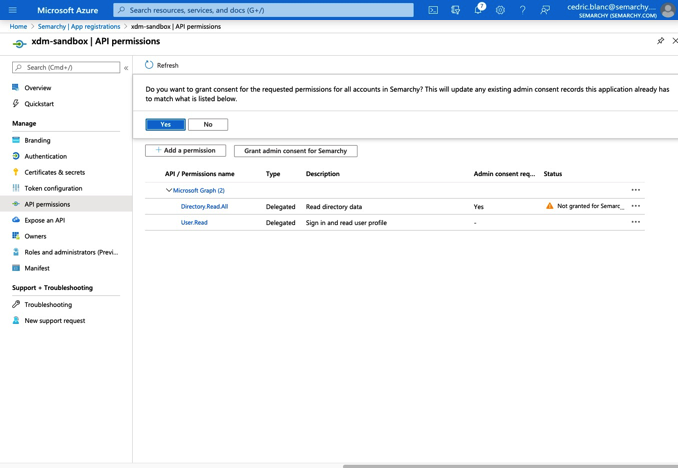
Click the Grant admin consent for… button and then click OK to confirm.
-
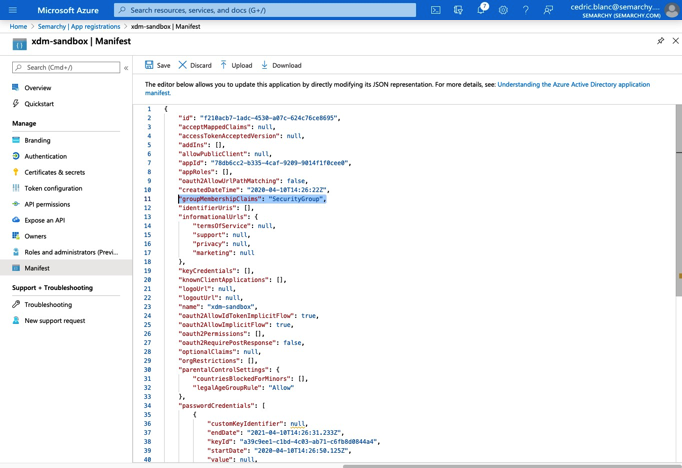
Under the Manage section in the navigation pane, select Manifest.
-
In the editor, search for the
groupMembershipClaimsproperty, currently set to null. Change its value toSecurityGroup.
-
Click Save.
-
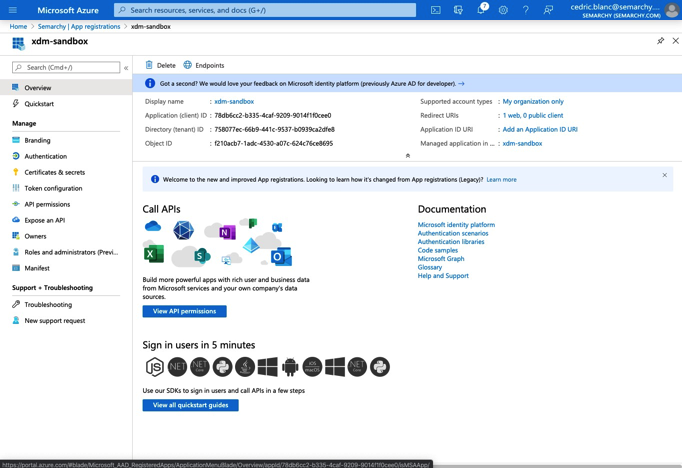
In the navigation pane, select Overview. In the Essentials section, note the Application (client) ID value, as it will be used as the client ID later in the configuration.
-
Select the Endpoints button. From the side sheet that appears, copy the URL of the OpenID Connect metadata document. This value will be used as the Issuer URL later in the configuration.
You should only copy the part of the URL until 2.0, as shown below.
|
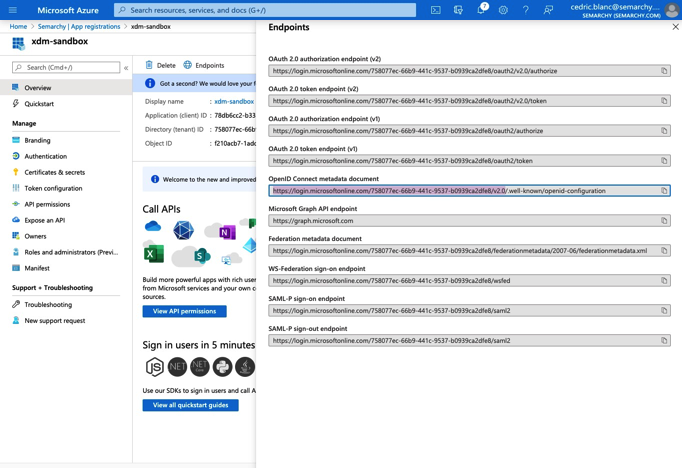
At that stage, you should have the three following values:
-
Client ID: the Application (client) ID on the App registration Overview page.
-
Client Secret: the value of the secret created on the App registration Certificate and secrets page.
-
Issuer URL: the OpenID Connect metadata document copied from the App registration Endpoints side sheet.
Identify ME-ID groups to use in Semarchy
Semarchy xDM uses roles that need to be mapped on groups in Microsoft Entra ID. You must identify the user groups and their corresponding roles in Semarchy.
-
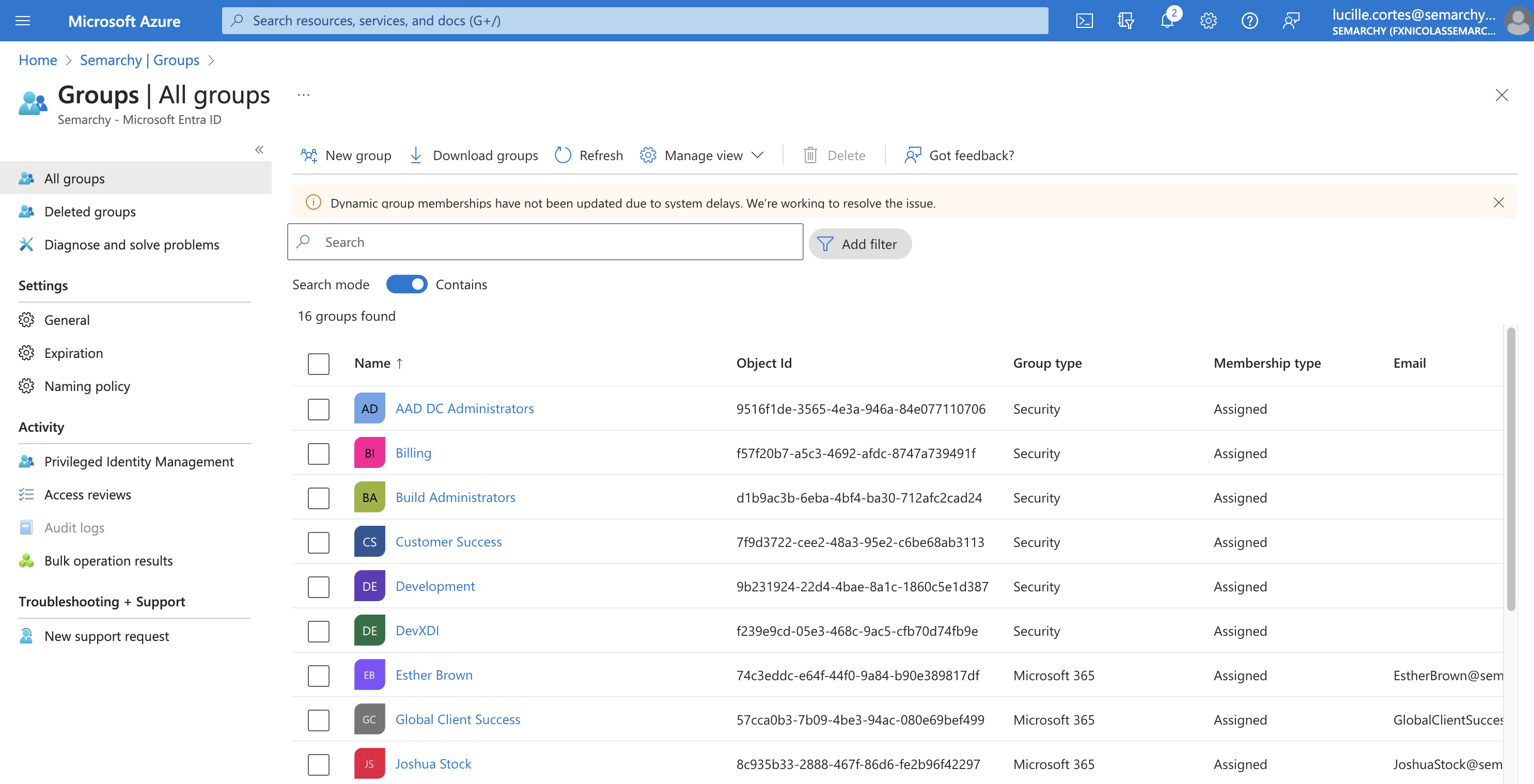
In the Azure portal, select Microsoft Entra ID.

-
Under the Manage section in the navigation pane, select Groups. Identify the groups that you want to map on specific roles and note their Object Id value.
Configure Semarchy xDM to use ME-ID
-
Access the Semarchy xDM Welcome page, open Configuration, and then select Identity Management.
-
Click the
 Add provider button.
Add provider button. -
In the Provider type field, select OpenID Connect.
-
In the Name field, enter an identity provider name and save your changes when prompted to do so.
-
In the identity provider editor, enter the following values:
-
Issuer Identifier: the value of Issuer URL in Microsoft Entra ID (see Register the application in ME-ID)
-
Client ID: the value of Client ID for the application in Microsoft Entra ID (see Register the application in ME-ID)
-
Client Secret: the value of Client Secret created in Microsoft Entra ID (see Register the application in ME-ID)
-
Logout URL: https://login.microsoftonline.com/common/oauth2/logout
-
Additional Scopes: email,profile
-
Username Claim: preferred_username
-
-
Note the value of the Redirect URL property, which you will declare in Microsoft Entra ID. This value is designated below as redirect URL.
-
Click the
Save button.
-
Select the Roles Mapping tab.
-
For each group that you identified in Microsoft Entra ID, click the Add Role Mapping button and enter the following details for the mapping:
-
Provider role: name of the role in Microsoft Entra ID.
-
Mapped role: corresponding role(s) in your Semarchy instance.
-
| Provider role | Mapped roles |
|---|---|
0450dc43-46d7-40d3-95d4-779a723f347a |
semarchyConnect,semarchyAdmin |
9b231924-22d4-4bae-8a1c-1860c5e1d387 |
semarchyConnect,dataSteward |
7f9d3722-cee2-48a3-95e2-c6be68ab3113 |
semarchyConnect,businessUser |
-
Save the identity provider.
Declare a platform for Semarchy xDM in ME-ID
You must now enter in Microsoft Entra ID the redirect URI of the identity provider you have defined in Semarchy.
-
In the Azure portal, select Microsoft Entra ID.
-
Under the Manage section of the navigation pane, select App registrations, and then select the application you previously registered.
-
Under the Manage section of the navigation pane, select Authentication.
-
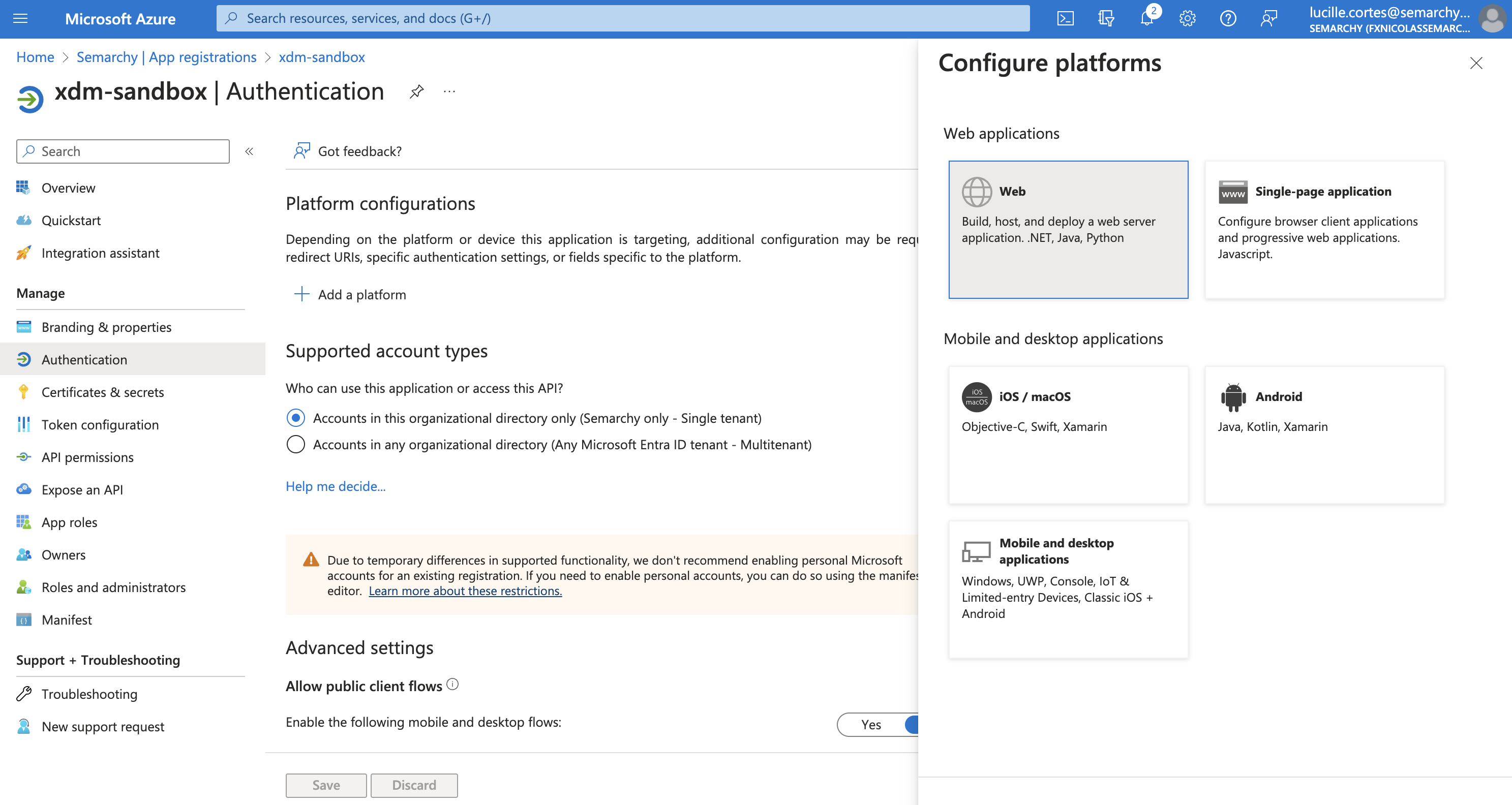
Select the Add a platform button, and then select Web.
-
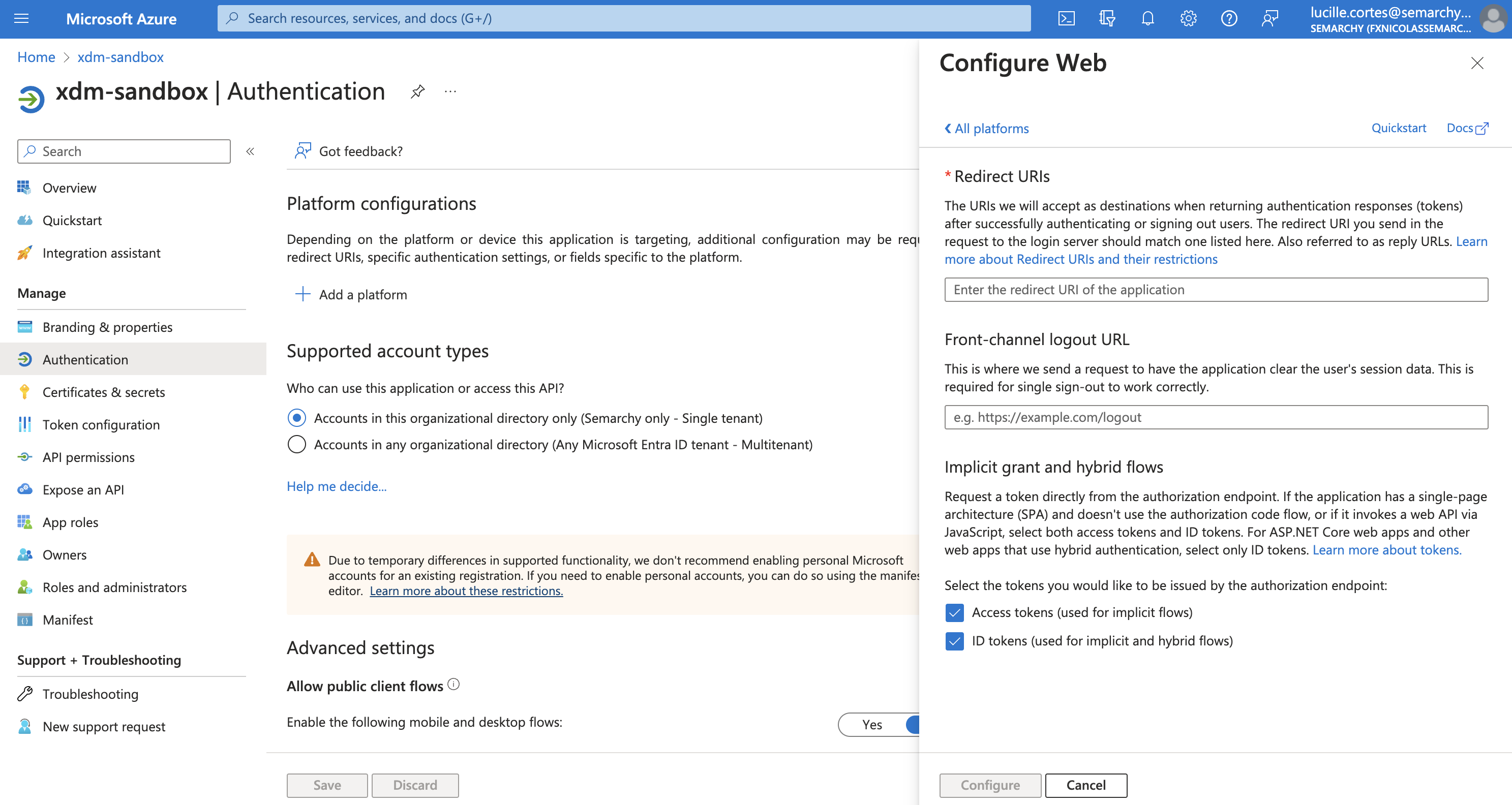
Under Redirect URIs, enter the redirect URL from the identity provider’s configuration in Semarchy.
-
Leave the Front-channel logout URL field empty.
-
Select the Access Tokens and ID Tokens checkboxes in the Implicit grant and hybrid flows section.
-
Click Configure to apply your changes.