| This is documentation for Semarchy xDM 5.3 or earlier, which is no longer supported. For more information, see our Global Support and Maintenance Policy. |
Secrets storage
A secret is sensitive data that need to be encrypted and optionally decrypted. For example, passwords, tokens, or keys to access resources such as databases, identity providers, etc, are secrets.
Known vs. possible secrets
Semarchy xDM has certain properties in its configuration which are:
-
Known Secrets: For example, passwords. These properties will always be encrypted or will have to be stored in an external secrets manager.
-
Possible Secrets: These properties are not encrypted by default, but the user may choose to secure their value. For example, the properties configuring a Kafka connection for a data notification may be secrets (e.g., the keystore password), or not (e.g., the request timeout). When a property is a possible secret, it appears as a field that allows making the value secret.
Manage secrets
The below screenshot shows a possible secret: JMS Username, and a known secret: JMS Password.

Note that:
-
The JMS Password known secret appears as a password field. It is impossible to retrieve its value in clear text form. It has an
 Edit Secret button to modify the secret value.
Edit Secret button to modify the secret value. -
The JMS User possible secret appears with a
 Make Secret button to make its value secret. Once the value is made secret, this field will behave as a known secret, as shown below.
Make Secret button to make its value secret. Once the value is made secret, this field will behave as a known secret, as shown below.

| Once a value is made secret, it is no longer possible to retrieve it in clear text form. |
Edit secrets
The Secret Value dialog allows you to edit a secret value.
To edit a secret:
-
In the Secured With field, select the KMS or secrets manager that you want to use for your secret.
-
To store the secret in Semarchy xDM in an encrypted form, select the current key management service (KMS) to encrypt it. It appears in the list as an alias prefixed with Encryption.
-
To use a secret stored in an external secrets manager, select the current secrets manager to encrypt it. It appears in the list as an alias prefixed with Secrets Manager.
-
-
Enter or define your secret:
-
If you have selected an encryption KMS, enter the value of your secret in the password field and then click OK.
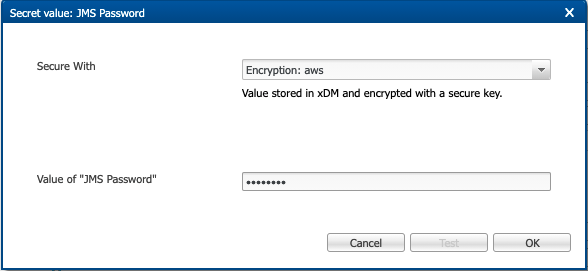
-
If you have selected a secrets manager, enter the alias of the secret stored in the secrets manager. If the secret is a JSON object, enter the property in this JSON object that contains the secret value.
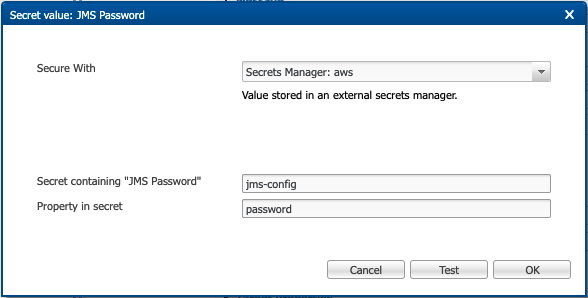
For example, in the example above, the
jms-configsecret contains a JSON object in the following format:Example 1. jms-config JSON contents{ "user": "myusername", "password": "xxxxxxxxx", }The Test button allows you to query the secrets manager to confirm that a secret can be read with this configuration.
-
-
Click OK to save the changes.
| For a possible secret, an additional Reset to plain text button clears the secret value and allows you to re-enter a plain text value. |
|
Switching between KMS and Secrets Managers by changing the value of the Secure with field does not:
When changing the secrets management method (Secure with), the secret previously stored in Semarchy xDM is lost. The only exception is the following: If a secret that was encrypted with a KMS that is still configured but no longer current, you can re-encrypt it with the current KMS by editing it and clicking OK without touching its value. |