| This is documentation for Semarchy xDI 2024.1, which is no longer actively maintained. For more information, see our Global Support and Maintenance Policy. |
Getting started with Kerberos in xDI Designer
This page contains information to help you get started with Kerberos in Semarchy xDI.
Overview
This page describes how to create Kerberos Metadata to store Kerberos information, such as the various principals and keytabs, in a central location. This information is then used in other components that support Kerberos authentication.
Create the Metadata
To create a Kerberos Metadata, launch the Metadata creation wizard, select the Kerberos Metadata in the list and follow the wizard.
Then, configure the server and principals properties.
Server properties
The server node is the root node of the Metadata.
It represents the global Kerberos properties shared with all the principals.
Below, an example of a server node:
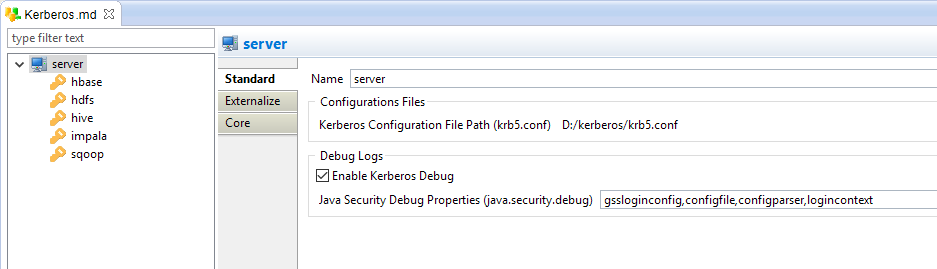
The following server properties are available.
| Property | Description | Example | ||
|---|---|---|---|---|
Kerberos Configuration File Path |
Path to the Kerberos configuration file.
|
D:/kerberos/krb5.conf |
||
Enable Kerberos Debug |
Optional debug property that allows to print more information in the Designer and Runtime consoles when performing Kerberos connections. |
|||
Java Security Debug Properties |
Optional comma separated list of debug values that should be returned by Java. |
gssloginconfig,configfile,configparser,logincontext |
Principal properties
Under Kerberos, an account in called a 'principal'.
In the Kerberos Metadata, you can add as many principals as required, representing your different services, organizations, …
To add a new Principal:
-
right click on the server node
-
choose
new > Kerberos Principal
Below, an example of a principal node:
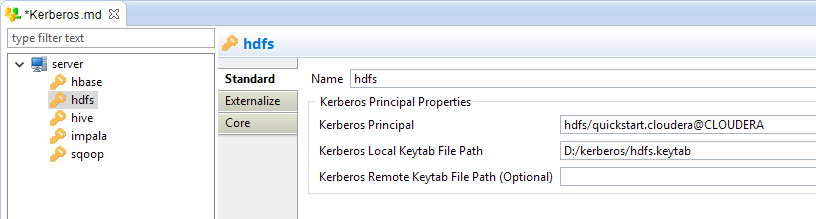
The following properties are available:
| Property | Description | Example |
|---|---|---|
Name |
Logical label (alias) to identify the Principal.
|
hbase |
Kerberos Principal |
Kerberos Principal name.
The Kerberos Principal must meet the standard Kerberos Principal syntax, that is the following: This property is mandatory. |
|
Kerberos Local Keytab File Path |
Local Path to the Keytab file associated to the Principal. |
|
Kerberos Remote Keytab File Path |
Optional remote Path to the Keytab file associated to the Principal. |
|